The simplest IT improvements with the biggest ROI for 2021
Happy New Year. If, like us, you’ve started 2021 full of optimism, you’ll want to get ready for all the opportunities and challenges it may throw your way. We’ve listed here what we think most businesses should be focusing on, to help make sure that happens.

Disaster Recovery Plans. Have You Tested Yours?
Research now shows that more than 90% of businesses have some form of disaster recovery plan to ensure business continuity following a natural disaster or cyber-attack. Sadly, only 25% have tested theirs to check it works. This is a big mistake made by many companies because without doubt, it’s better to reveal your vulnerabilities now, rather than during a costly disaster. Trialling your DR strategy ensures that each employee knows their role and irons out any tiny flaws so that nothing impacts business continuity. As more people work flexibly and perhaps from home, it’s important to ensure that any DR plan can be effectively activated by people working as they are now, and not as they were when the plan was first created.
Security Training: Investing in Your Employees Always Adds Value
Despite investing huge budgets in technology to protect them from cybercrime, many businesses still have a gaping hole with regard to employee training. Every business should ensure the whole team understands the threat landscape. Your team won’t just inherently know how to react to scams. In fact, research shows that nearly 40% of employees, without training, fail phishing tests.
To put that in context, phishing is still one of the biggest threats to your data security and ultimately your reputation and profits. 84% of SMBs are targeted by phishing attacks. Investing in your employees is never a waste.

Your Business Continuity Plan: Is it Set in Stone?
The trouble with emergencies is they have their own schedule. They won’t necessarily happen when it’s convenient. For this reason, it’s imperative to have a well-documented plan, accessible to all, rather than just a select few, in the event of an emergency. Formally documenting your plan will encourage far more critical thinking from all departments, and gain input on its practical application from a much greater volume of employees. Formal documentation makes it easier to amend and adapt the plan as the business and its infrastructure changes shape. It also ensures that the plan fits with latest best practise for business continuity and can be used to demonstrate compliance when necessary.

The average cost of recovering from a data breach is £2.9 million.
A Regular Patching Schedule: Achievable, Proactive Protection
According to research, together, missed system patch tests and software patch tests account for nearly 60% of data breaches. A patch test schedule is one of the clearest ways to be proactive about security. Many businesses (even well-publicised huge enterprises) find that identifying and deploying patches manually can be complex, challenging and time consuming. It is, however, becoming easier to automate with patching management software or simply outsourcing everything to specialists. It’s absolutely worth it, given the average cost of recovering from a data breach being £2.9 million. A little bit of preparation in this area offers a huge amount of ROI.
MFA and 2MFA: Double the Hurdles for Cyber Attackers
If you haven’t already, please invest in two-factor authentication. It’s really simple to get up and running. Not only does it help protect against phishing (scams that encourage employees to reveal their passwords, accounting for the biggest percentage of data breaches) it saves money and time wasted by your IT team.
With two-factor authentication, employees can easily and simply reset passwords themselves rather than needing support. This solution is particularly helpful as more employees work from home and need to log in remotely. It’s also a system that easily alerts employees on a separate device if an attempt has been made to log into their account.
Cyber Essentials: Simplifying Security with a Framework for all Businesses
If you are unsure how to develop a roadmap to better security, both Cyber Essentials and Cyber Essentials Plus are a great starting point. Cyber Essentials is a government framework and accreditation project which supports businesses in meeting a minimum standard of security in order to tender for government projects.
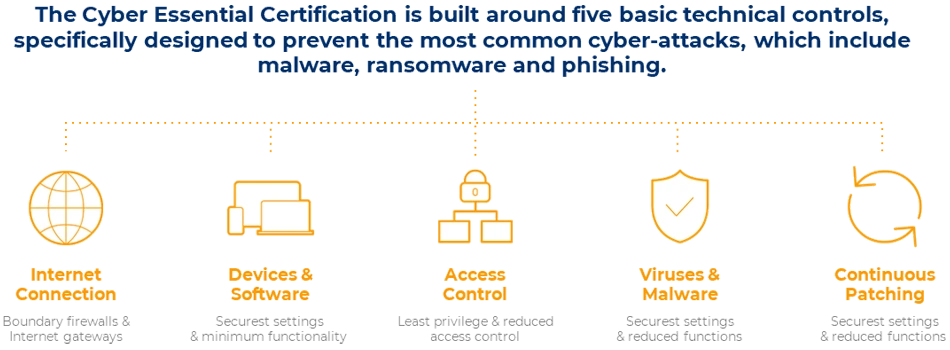
It was launched to ensure that any business hoping to win government contracts had the correct amount of measures in place to ensure against data and security breaches. It offers three big benefits: ensuring that your business is adequately secure, inspiring customer confidence regarding your commitment to security and allowing the opportunity to tender for government contracts should the right one be identified.
Cyber Resilience: Identify, Evaluate, Defend and Recover
Cyber Resilience breaks down a businesses ability to be able to identify, evaluate, defend against, and recover from cyber-attack. By considering each aspect required to survive in a landscape rife with threats, businesses can assure themselves and their stakeholders of their resilience across every aspect of an attack. This is particularly important as so much research now exists regarding the impact felt by businesses up to three years post attack and, also, the well-documented money saved by businesses who have been able to identify and defend against attack early on.
It seems perilous for any business to assume they are immune to successful attack, so preparing for the statistically inevitable really does increase every business’s chance of success.
Simple and Secure On-Boarding and Off-Boarding
With employees working on different devices in different locations all across the globe, smooth and secure onboarding and offboarding has never been more important. Luckily, with a wealth of solutions now available to us all, such as zero touch deployment and all that O365 has to offer, it’s also never been easier to get new employees, contractors and offices up and working and closed down seamlessly.
If you don’t have the systems in place, there are many affordable and scalable options open to you to allow you flexibility in recruiting the right talent for your business, wherever that may be.
